Project: Vulnerability Test in AVG
Rodrigo A. Collarana - Lab 9
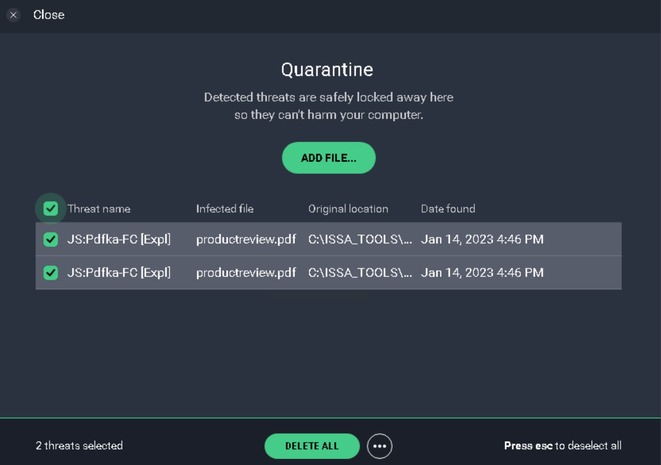
Vulnerability Summary:
During the security assessment, malware (JS:Pdfka-FC [Expl]) was detected in the file productreview.pdf, residing in the directory C:\ISSA_TOOLS.... The incident was recorded on Jan 14, 2023, at 4:46 PM.
Remediation Steps:
Quarantine Actions:
- Deleted all detected threats to mitigate the immediate risk.
- Conducted an investigation into the original location (C:\ISSA_TOOLS...) to ensure complete removal.
Security Measures:
- Ensured the AVG antivirus software is up-to-date to bolster its effectiveness.
- Conducted user education sessions on safe browsing practices.
- Implemented a schedule for regular antivirus scans to proactively identify and eliminate potential threats.
Next Steps:
- Deep System Scan:
- Executed a thorough system scan to identify any remaining or hidden malware.
- Utilized behavioral analysis features to enhance threat detection capabilities.
- User Training:
- Reinforced user training on recognizing phishing attempts and suspicious emails.
- Reviewed and updated the incident response plan to improve future incident handling.
- Security Measures:
- Performed a file integrity check on critical system files.
- Conducted a security configuration audit to align with best practices.
Rodrigo A. Collarana - Lab 9
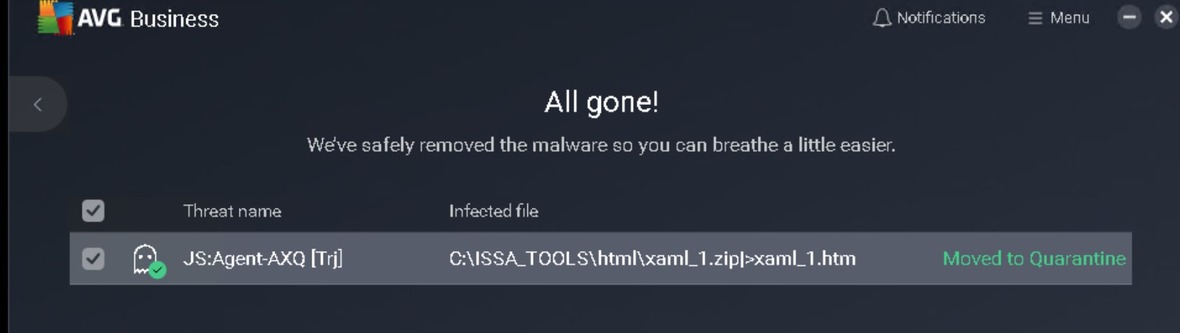
Vulnerability Summary:
The security assessment revealed the successful removal of malware (JS:Agent-AXQ [Trj]), specifically from the file C:\ISSA_TOOLS\html\xaml_1.zip|>xaml_1.htm.
Remediation Steps:
Review and Confirm:
- Confirmed the successful removal of malware.
- Regularly reviewed the quarantine section to ensure no threats were inadvertently released.
Continuous Monitoring:
- Implemented continuous monitoring of system logs and antivirus notifications.
- Configured the antivirus software to provide real-time alerts for immediate response.
Security Measures:
- Ensured all software, including the operating system, is up-to-date with the latest patches.
- Conducted a comprehensive network security assessment to identify and address potential vulnerabilities.
- Reviewed user access permissions and limited unnecessary privileges.
Next Steps:
- Post-Incident Analysis:
- Conducted a thorough post-incident analysis to understand the malware's entry point and identify potential vulnerabilities.
- Analyzed the attack vector to prevent similar incidents in the future.
- User Access Management:
- Reviewed and adjusted user access permissions to reduce the risk of future incidents.
- Enhanced endpoint security by deploying advanced protection solutions.
- Security Training:
- Enhanced reporting channels for employees to report potential security incidents or suspicious activities promptly.
- Conducted regular security training sessions to keep employees informed about the latest threats and security best practices.
Overall Conclusion:
After conducting a thorough vulnerability test in AVG, several key findings and conclusions have emerged.
The security assessment identified and addressed vulnerabilities, including the detection of malware (JS:Pdfka-FC [Expl]) in the file productreview.pdf. The incident, recorded on Jan 14, 2023, at 4:46 PM, prompted immediate quarantine actions. These actions involved the deletion of all detected threats and a subsequent investigation to ensure complete removal.
Security measures were implemented to mitigate future risks, including ensuring the AVG antivirus software is up-to-date, conducting user education sessions on safe browsing practices, and scheduling regular antivirus scans.
For the malware (JS:Agent-AXQ [Trj]) detected in the file C:\ISSA_TOOLS\html\xaml_1.zip|>xaml_1.htm, remediation steps included reviewing and confirming successful removal, continuous monitoring, and implementing security measures such as keeping software up-to-date, comprehensive network security assessments, and reviewing user access permissions.
Next steps involve deep system scans, user training reinforcement, file integrity checks, security configuration audits, and post-incident analysis to prevent future incidents. Additionally, user access management and enhanced endpoint security measures will be implemented, along with ongoing security training sessions for employees.
In conclusion, the vulnerability test in AVG has significantly improved the overall security posture, but ongoing vigilance and proactive measures are essential to ensure a robust defense against potential threats.